Connecting Silos and Bridging the Communication Gap between Internet Technology and Physical Security Departments
The Silo Mentality is defined by the Business Dictionary as a mindset present when certain departments or sectors do not wish to share information with others in the same company. This type of mentality will reduce efficiency in the overall operation, reduce morale, and may contribute to the demise of a productive company culture.
In the security industry, silos are often the buzzword we hear when talking about Information Technology (IT) and Physical Security. Each department, usually made up of like-minded individuals, has its own knowledge base as well as its own set of values, work ethics, and work experiences. With each having its own language per say, it’s not hard to see why they have a hard time communicating. In fact, productive dialogue, on the surface, can seem insurmountable.

Why is there a communication gap?
Different Backgrounds/Knowledge Gap
IT and Physical Security teams have vastly different professional backgrounds and personalities. IT personnel can often be introverted, thriving on hours of alone time. Their focus is on the company’s complicated network, writing code, programming, and assuring all systems stay online and connected to the Internet. They also work to ensure the network is protected from cyber-criminals and internal/external breaches. On the other hand, Physical Security personnel tend to be more extraverted. In fact, many come from law enforcement or the military. Their focus is on human behavior, protecting employees and the public, as well as monitoring and securing physical environments.
Different Goals and Objectives
Each department has their own set of goals and objectives which roll up into the overarching security goals of the organization. Regarding the Physical Security team, their main objectives are to plan and manage for the protection and safety of employees, company assets, and the public. Their priority goal is to ensure that all personnel and the public are safe. The second priority goal is to secure company assets. Regarding the IT team, their main objectives are to provide a robust and secure IT infrastructure that supports on-demand access to information. Additional IT goals are to deliver advanced capabilities which foster collaboration, knowledge management, and analytics for company decision making. While each department supports the main security goals of the organization, they individually have goals and objectives which make their contribution different.
Limited Information
In today’s world, entire departments are bombarded with an ever-increasing amount of data. Unfortunately, they still often lack the information necessary to do their jobs well. Why is this happening? Regarding company security, each department, IT and Physical Security, hold a piece of the information pie. However, due to a lack of information sharing, a complete picture cannot be realized. Missing information leads to a lack of context, and obvious signals can be missed. The result is a complete breakdown in an organization’s security posture.
If companies want to make better decisions regarding security, they must foster productive information exchanges between these two departments. In fact, sharing of information is critically important to achieving any organization’s security goals.
Connecting Silos
Understanding Responsibilities
Both IT and Physical Security have integral roles in an organization’s security posture. IT is responsible for protecting data, as well as its efficient movement and safe storage. Physical Security is responsible for protecting the infrastructure and personnel tasked with protecting the data. There is a definitive common mandate here. Even if they function as silos, they are complementary pieces to the puzzle.
Keep in mind, businesses and departments don’t do business. People do. The human element is almost always an inherent challenge. Before the security of anything, as individuals we are most interested in our own job security. When both parties embrace this, differences can be displaced, and common commitments realized.
Building a Bridge through Common Language
One of the very first hurdles to overcome is finding a common language. With the advancement of IP security technology, Physical Security has not so quietly converged with IT. The language of Physical Security now includes bandwidth, CPU, storage, and more. It sounds complicated. However, at its roots, we’re simply talking about information/data flows.
The Whole Story
IT teams are challenged by placing security technologies on the corporate network because video consumes a massive amount of data. This in turn, creates tremendous noise from an IT management perspective and can hinder IT’s objective – safe and rapid transit of data.
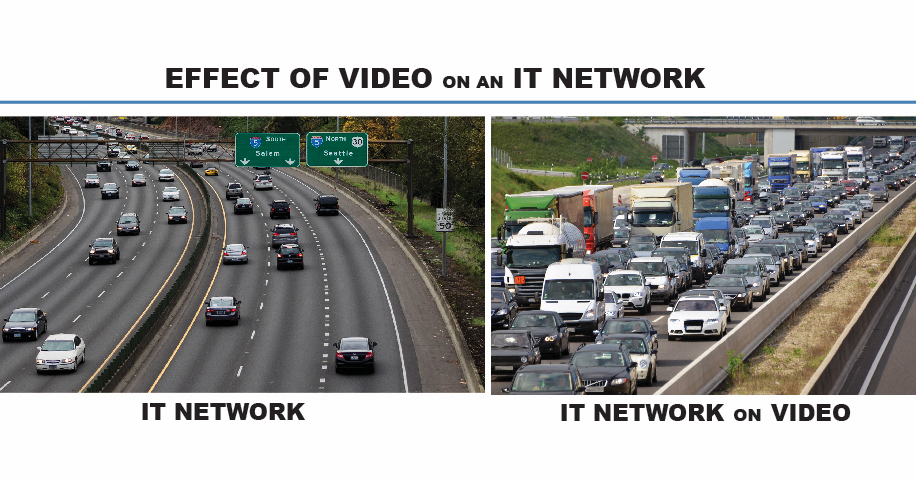
What’s more, each IP device has attack vectors for nefarious individuals to infiltrate. These vectors must be vetted and vulnerabilities addressed to assure the corporate network remains secure.
Now let’s assume IT has overcome these challenges, and all security technologies have been added to the network. In this scenario, IT has likely connected all IP security devices and applications and set up monitoring to assure they are on. The problem is, knowing the technologies are on, does not mean they are operating and available, i.e. recording video, ample data storage capacity available, sufficient UPS battery life, etc. How are Physical Security teams going to be confident in their operation?
The fact is, Physical Security needs real-time information regarding the availability, health, and performance of all their security technologies. Without it, they can’t be confident in their operation. And, therein lies the rub.
Most monitoring tools have not been designed to monitor the availability, health, and performance of IP security assets. Why? It takes experience to understand how IP devices and applications move and store data. Furthermore, there are no standards from security edge devices from which IT can develop a suitable policy or process. Finally, IT teams do not always have the resources to adjust to the needs and nuances of IP security inventory.
Enter Vunetrix
Vunetrix is a purpose-built monitoring tool for IP security assets. The software has been custom designed to detect health and performance anomalies with IP security technologies. We believe it’s imperative for Physical Security teams to deploy their own monitoring and assessment systems. Vunetrix offers an independent and comprehensive view of the entire security network and all its connected IP security devices and applications.
Here’s the best part. When Physical Security can monitor their own IP security inventory, IT doesn’t have to. Adding this to understanding responsibilities, and the bridge is nearly built. The last piece to the equation is building a cooperative strategy.
Creating A Unified Vision
Connecting department silos is not an easy task. However, the avoidance of these issues will be detrimental to your organization. Can you imagine trying to row a boat while part of the team is trying to turn right, and the other part is trying to turn left? Impossible, right? There’s nothing more powerful than having all employees rowing fiercely in the same direction towards a common goal.
“Good thoughts have much to do with good rowing. It isn’t enough for the muscles of a crew to work in unison; their hearts and minds must also be one.”
-George Yeoman Pocock
With the ever-increasing reliance on IT security technology, organizations will benefit by having a single person overseeing both departments. Instead of retaining the traditional roles of Chief Security Officer (CSO) and a Chief Information Officer (CIO), forward looking organizations are combining these roles into a single CISO position. This organizational design allows a unified security vision to be effectively bridged between the Physical Security and Information Technology silos.
To be sure, organizations destined to succeed in this volatile, ever-changing, and complex security culture will develop and regularly communicate an aligned vision. These visions don’t have to be overly complex. They do however, need to be something that the teams can connect to. A clearly defined and unified vision, along with collaborative information exchange between IT and Physical Security is how the best organizations are going to thrive and meet their security goals well into the next century.
