 Monitoring IP Security Inventory – A Missing Link in Cyber Security
Monitoring IP Security Inventory – A Missing Link in Cyber Security
The Center for Internet Security (CIS) has identified 20 CIS Controls that are a prioritized set of actions that collectively form a defense-in-depth set of best practices to mitigate the most common attacks against systems and networks. These controls have been developed by a community of IT experts who apply their first-hand experience as cyber defenders to create these globally accepted security best practices. The experts who developed the CIS Controls come from a wide range of sectors including retail, manufacturing, healthcare, education, government, defense, and more. (Click here to download the eBook containing details on the 20 identified CIS controls.)
What’s the missing link?
All 20 CIS Controls are indeed extensive and cover the majority of inroads a cyber-criminal may utilize for a point of attack. However, what they don’t include and should is a very basic and necessary step every organization must take to protect the company from harm.
Introducing Physical Security Equipment Monitoring
Do you have a way of monitoring your security technology for availability and performance? If not, how confident can you be that your organization is protected? Take for instance the case in which a company chooses to provide a backup battery power supply for when a power failure occurs. This is common sense, right? Doesn’t it also make sense to monitor endpoints to make sure they are still functioning? What about monitoring applications to assure they are operational?
Reduce and Mitigate Risk
Jerry Wilkins from Active Risk Survival shares a very interesting formula which should raise some eyebrows in the security industry.
![]()
How does your organization reduce and mitigate risk? Simply stated, through countermeasures. Countermeasures include all of the technological, educational, and social tools in place and used to protect a organization’s people and assets as well as the public at large. In addition, countermeasures are amplified when the tools are used to their fullest intent.
Here’s the concern. When countermeasures don’t include monitoring technologies to:
- Establish baselines for security inventory
- Monitor security inventory for availability
- Monitor security inventory for performance
- Alert when anomalies are present
- Alert when security inventory states change
how can you be confident in their operation? And, herein lies the rub.
The Modern Security Network Explained
At the heart of every modern security management system is the network. It’s made up of a variety of devices and software applications connected through IP (Internet Protocol) communication. Some of these include SNMP, WMI, and API. (View Definitions List Here) These open protocols are what makes it possible to communicate with and monitor security inventory. The monitoring is performed by sensors and each device and/or application has a specific set of available sensors written into the technology by the manufacturer. A monitoring tool communicates with these sensors through Internet Protocols and relays availability and performance metrics. The sensors ensure if security inventory goes down, the Security Team receives instant notification. Notifications can be delivered via email, text message, or pager. Security Teams can now quickly troubleshoot and resolve faults the moment the state changes, proactively reducing the threat of physical security breaches.
Below is a list of IP security inventory which can and should be monitored for availability, performance anomalies, and state changes. (This is not a complete list)
Physical Security Inventory
- Emergency Phones and Intercoms
- Alarm Panels
- Access Control Panels
- IP Cameras
- Video Management Services
- Servers (NVR/PACS)
- Network Switches
- Routers and Firewalls
- SMART UPS
- IP Environmental Monitoring Hardware
Download the Physical Security Essential Monitoring List Here.
Security Network Performance “Know Your Normal”
All IP devices/applications supporting a physical security environment make up the entire security network. To keep IP security inventory up and running as smoothly as possible, a few basic conditions are required. Security Teams must understand and identify how data is exchanged between devices/applications. The key is understanding the metrics for healthy/normal running IP security inventory, benchmarking these measurements, and setting thresholds and alerts.
For example, it’s important to understand how much bandwidth specific devices use when operating normally, what the traffic flow looks like in different parts of the network at different times of day, and, what kind of CPU and memory usage is normal for servers. Based on these “normal” metrics, Security Teams set thresholds and alerts. When values go above or below the “normal” values, monitoring tools will alert Security Teams to the potential problem.
When Security Teams work proactively to detect and acquire specific information relevant to the availability and performance of their security inventory, troubleshooting is effective and timely. Teams spend less time looking for potential issues and are automatically alerted to problems they may not have realized were present on the network. This ultimately provides more efficient use of manhours and allows Security Teams to direct their time to other meaningful tasks.
In short, when Security Teams have a competent monitoring tool in place, they know, when there’s a problem, why there’s a problem, and how to respond. Learn more about “Know Your Normal.”
Security Network Anomalies
When, using a competent monitoring solution, it’s possible to get a view of the entire security network on one single-view dashboard. The information obtained from monitoring physical security inventory can help you make adjustments to prevent critical failures such as loss of data. Here are some examples of potential issues you can detect in real-time when monitoring physical security inventory.
Physical Security Inventory Potential Issues
Emergency Phones and Intercoms
Alarm Panels
Access Control Panels
IP Cameras
Video Management Services
Network Switches
Routers and Firewalls
SMART UPS
IP Environmental Monitoring Hardware
Servers (NVR/PACS)
Emergency Phones and/or Intercoms have lost power or connectivity.
Alarm Panels have lost power or connectivity.
Access Control Panels have lost power or connectivity.
Cameras are malfunctioning, misconfigured, or not enabled.
Video is not recording. Cameras are not responding.
Network switch is experiencing bottlenecks.
Routers and Firewalls are failing.
Backup battery power is insufficient. Line voltage has been lost.
Temperature/humidity of the server rooms is out of range. Water is present. There’s a change in atmospheric pressure.
Servers are in pre-failure state and need replacing. Disk space is low. Temperatures are too high.
Physical Security Inventory Monitoring Features and Benefits
With the advancement of IP security technology, it has become possible to access in-the-moment insights about security inventory and streamline device/application management. Security Teams can now deploy a monitoring solution which integrates and manages all of their security inventory across multiple geographies through a single-pane-of-glass. What’s more, most competent monitoring tools enable remote management such as:
- Start a process on a remote device
- Schedule a process to run at a particular time
- Reboot a camera
- Get a list of applications installed on a local or remote server
- Query the Windows event logs on a device
All of these actions and insights improve intelligence, enhance operations, and increase overall visibility of the security network. The best monitoring solutions are custom built for security and can be deployed on any security network and optimized in less than a week. Additionally, a competent monitoring tool will have scalable technology which allows any organization to deploy a customized solution to meet their unique demands, from small business to enterprise to carrier. In the end, the time saved through monitoring and automation can be applied to more meaningful safety and security efforts.
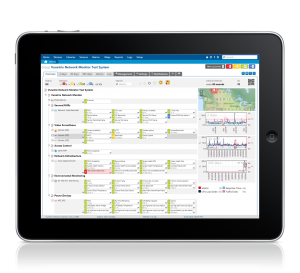 DASHBOARD – Monitor all of your physical security inventory from one single-view dashboard
DASHBOARD – Monitor all of your physical security inventory from one single-view dashboard
Dashboards are simple yet extremely powerful. Most device/application monitoring tools come with a variety of dashboards which displays network devices/applications as lists or hierarchical trees. Among other things, dashboards let you visualize at a glance which devices/applications consume the most or least amount of bandwidth, and the devices/applications that cannot be reached via ping. (View Ping Definition Here) Dashboards present information in a way easy to understand by all.
MAPS – Monitor all security inventory from multiple vendors in multiple locations
A mapping function on the monitoring tool makes it easy to see how network devices/applications are related to one another. Maps offer a graphical representation of your network’s geography. They allow you to visualize the arrangement of all the devices/applications connected to and exchanging data via the network. Faulty devices/applications can be spotted at a glance, which include status icons for each and every device/application. In some cases, these maps allow for correlations to be identified which cannot be determined by a simple device/application list. You can also use maps to check the stability of your network and thus ensure the network remains operational even if an individual connection fails. Finally, network map knowledge can be used to evaluate the performance of investments and select the right hardware when it comes time to expand or replace inventory.
DEVICE MANAGEMENT – Optimize, Reduce Cost, and Increase ROI
One way to optimize network device management is by deploying a tool that automatically searches the network for current data and new devices. It is no longer necessary to create laborious Excel sheets for devices/applications. You also eliminate the need to enter information into the management software manually. Instead, users receive an up-to-date display of available network devices/applications and status information automatically.
SERVICE AND MAINTENANCE – Enhance the effectiveness and efficiency of your security operations
Network device management is vital to successful device service and maintenance. Status overviews and real-time database information allow for maintenance to be planned from one central location, and device swaps to be prepared in advance. In the event of a problem, you can troubleshoot all devices remotely. When information is centralized, error management becomes a simplified process.
PROMPT ERROR NOTIFICATIONS – Detect failures inside your security network
If a device/application malfunctions, an error message appears on the dashboard and an alert is sent by email or SMS. This saves Security Teams time lost in having to check devices manually. Network device monitoring runs in the background and keeps a constant eye on all devices. Additionally, alerts can be customized by priority, job function, and time of day. Alerts can also be automatically escalated when appropriate. There are even customizable nag alerts.
Security Teams won’t be caught unaware when devices lose connectivity or behave abnormally. Instead, they can immediately intervene when the software detects an anomaly, before an environment is compromised and before a security event occurs.
REPORTS – Access automated and on-demand reporting
A competent monitoring tool allows Security Teams the ability to create custom reports perfect for sending detailed information to technicians or managers. These reports can be generated automatically. Device/application availability and performance reports can also be automatically sent to invested users/technicians/Integrators/management on a scheduled basis. What’s more, a periodic overview of the security network’s performance, or figures which have resulted in problems in the past, can be created and delivered.
COMPLIANCE – Manage compliance mandates effectively and efficiently
Monitoring software should automate time-consuming tasks and deliver real-time, holistic visibility into device/application availability and performance. The goal is to ensure the security of all areas and accurate record keeping. With the correct alerts, Security Teams use fewer resources to ensure compliance and consistent performance of security inventory. A competent monitoring solution with help Security Teams guarantee uptime and streamline compliance reporting in real time. A proper monitoring tool will deliver information immediately for quick and appropriate responses, including the deployment of law enforcement and the required notification of regulatory agencies.
In summary, we like to say that Physical Security Network Monitoring (PSNM) is the missing link in Cyber Hygiene and Security Best Practices. Coming back full circle, it’s increasingly challenging to be confident in your security technology’s availability and performance. Monitoring tools assure system availability and performance.
Always On, Always Vigilant!
For more information about this topic, download our white paper, “Addressing the Challenges and Complexities Facing Physical Security Networks”, or give us a call. Our team of experienced Security Practitioners has more knowledge about this topic than any other PSNM company in the industry today. Contact Vunetrix Today!
