The basic principles of physical security systems have been around for decades and have not changed. Access control, surveillance, intrusion detection, and alarm triggering form the base for most well-designed systems. What has changed, is the technology driving physical security devices and applications.
Introducing the Modern Physical Security System
Over the past decade or so, we have seen a demand for security devices and technologies to become integrated and internet connected. Many organizations inside of every industry have digitized their physical security system and added IP security devices and applications. While these system advancements certainly come with advantages, there too are many challenges.
Connecting Disparate Devices and Technologies
Due to the digitization of vast components, modern security systems are often a patchwork of technologies, protocols, and a variety of devices from multiple vendors. The first challenge Security teams face is that they need to get all these disparate devices on a network. Then, they need to get that network configured and optimized. Unfortunately, getting the environment set up and configured is only the first hurdle.
The Newest Achilles Heel: The Network
Any device connected to the network poses a new point of failure for the modern security system. For example, lost data has become a huge factor. With video data now being recorded and stored digitally, if something goes wrong such as an unstable network or a failed server, video footage will get lost.
In addition, networks are subject to bottlenecks, band-width issues, and routing problems. All of these problems can pose a threat and compromise a security system. What’s more, if cyber criminals gain access to the network or devices, they have the ability to negate the entire system. This might involve shutting down critical cameras or gaining access to a building.
How Do You Prevent Network Anomalies and Cyber Attacks?
The truth is, you can’t completely circumvent these risks. Electronic devices will malfunction, networks will have bandwidth issues, and storage devices will reach capacity and fail. These are the unfortunate facts of a digital world. But what you can do is take preventative steps and set up alerts for when there is a failure or system anomaly. Enter network monitoring…
Monitoring the Physical Security System
 As with many industries, modern security systems have seen a convergence with traditional IT. The good news is that your security devices are now running on the same infrastructure as more operational IT devices such as switches, routers, servers, and so on. While this does add to the complexity of these systems, it also means you can monitor everything in one place, despite the disparate technologies.
As with many industries, modern security systems have seen a convergence with traditional IT. The good news is that your security devices are now running on the same infrastructure as more operational IT devices such as switches, routers, servers, and so on. While this does add to the complexity of these systems, it also means you can monitor everything in one place, despite the disparate technologies.
The same general steps that apply to monitoring traditional IT environments, also apply to monitoring a physical security system network.
- Establish the metrics for a healthy running system. We call this, “Know Your Normal.”
For example, how much bandwidth do specific devices use when operating normally? What does the traffic flow look like in different parts of the network at different times of day? What kind of CPU usage is normal for servers? - Based on the metrics from step 1, you can then set baselines, thresholds, and alerts. When values go above or below the normal values, the monitoring tool detects there is a problem, and sends an alert.
When using a good network monitoring solution, it’s possible to get a view of the entire network on one dashboard. Furthermore, the information you get from monitoring the network can help you make adjustments to help prevent loss of data or critical failures.
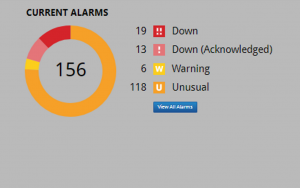 Network Abnormal Performance Alerts
Network Abnormal Performance Alerts
- Cameras not recording
- Hard drive space is low
- Hard drives are in pre-failure state and need replacing
- UPS battery life is low
- Security device performance is abnormal
- Services are hung, causing unresponsive applications
- Network switch is experiencing bottlenecks
Network abnormal performance alerts provide Security teams with the nature and location of the problem. These alerts can be configured for priority and job function, and escalated when appropriate. This way, the right people get the right information quickly, for a timely and intelligent response.
Network Monitoring Advantages
One of the advantages of network monitoring is that the kinds of systems you can monitor are quite varied, as long as the connected devices offer standard technologies (such as SNMP, NetFlow, WMI, and so on). While the monitoring approach remains the same – configure a sensor for a device and get statistics from that sensor – the actual network can look very different from one installation to another.
Another advantage is the Integration and management of your entire security network on a single platform. With the technology behind Network Monitoring, there is a better way to keep your finger on the pulse of all your security technologies, 24/7. Real-time status and performance insights, enhanced by connecting multiple technologies across multiple geographies, provide Security teams an effective method for accessing in-the-moment insights for security status and activity. This enables organizations in every industry to be proactive, avoid data losses, and fully maximize their initial investment of security technologies already in place.
And finally, armed with a deeper understanding of security system performance, coupled with real-time alerting, Security teams can respond to system performance issues immediately and proactively. In other words, with a good network monitoring solution in place, the right information gets to the right people quickly for a collaborative response before your environment is further compromised and before a security event occurs.
If you would like to learn more about Physical Security Network Monitoring, give the team at Vunetrix a call. We have an off-the-shelf monitoring solution built specifically for physical security that can deployed on any network and optimized in under one week. Call us today!
