Big data, IoT, business process management, and sophisticated monitoring aim to reduce risk and improve security, resource management, and decision-making at all levels of government and public transportation.
Introduction
In many ways, a perfect storm has been brewing in the physical security space for quite some time. Owners and administrators of IP security systems face ever-growing resource demands and are experiencing significant management and support challenges daily. Converging threats and burdensome complexity continue to menace organizations that are simply unprepared to face such threats. While IT professionals often focus on data protection and headline-grabbing cyber threats, security professionals must do what they can to protect property and people as well as ensure secure access and maintenance of high-value video. Read More










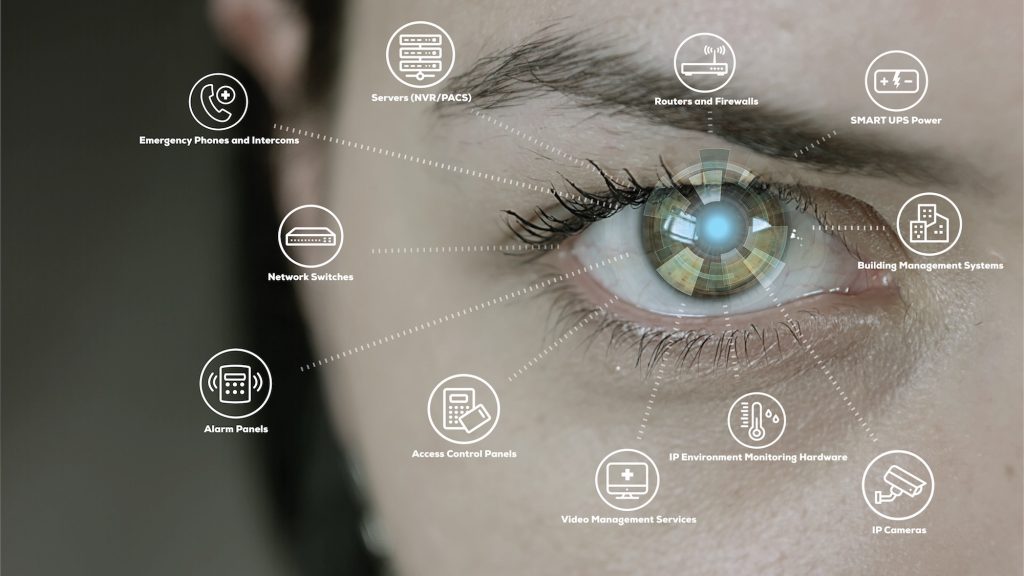
 Monitoring IP Security Inventory – A Missing Link in Cyber Security
Monitoring IP Security Inventory – A Missing Link in Cyber Security